
Endpoints serve as the primary interaction points enabling users, administrators, and customers to leverage the broader capabilities of a network infrastructure.
Endpoints include laptops, desktops, tablets, and smartphones being used to connect to a corporate network; Internet of Things (IoT) devices such as smart home assistants, watches, security cameras, tracking equipment, and medical devices; and Point-of-sale (PoS) terminals and kiosks that provide endpoint access for transactions and information lookup. Specialized equipment with processor chips and connectivity like industrial control systems, building management systems, vehicles, and diagnostic medical devices can also be endpoints. Managing security and controls for endpoints is critical in the modern network environment.
25% To 30% Of Breaches Originate At Endpoint
According to most estimates, around 25% to 30% of all breaches originate at the endpoint level. Examples of research highlighting this, include:
- Verizon’s 2020 Data Breach Investigations Report found that up to 30% of breaches involved endpoint privilege misuse, errors, or poor controls.
- According to a 2021 Forrester Research report, 25% of data breaches are associated with endpoint devices being compromised in some manner.
- Research by Enterprise Management Associates found that breaches instigated by endpoints accounted for 24% of all breaches amongst organizations surveyed.
- A SANS endpoint security survey from 2019 indicates that 63% of organizations saw endpoints being compromised and used as an initial access point by attackers.
Key Drivers Of Endpoints Being Origin Of Breaches
Key drivers of endpoints being the origin of breaches include phishing lures on endpoints, improperly secured devices, use of compromised endpoints as attack vectors, and vulnerabilities in endpoint software being exploited. Regardless of the precise percentage, securing endpoints is clearly a high priority for reducing organizational risk. Implementing endpoint detection, response, and controls, as well as protecting sensitive data on endpoints in the event the device is compromised, needs to be a key element of any cybersecurity strategy in today’s landscape.
Demand for endpoint security solutions is driven by factors such as the rise in remote workforces, bring your own device (BYOD) policies, sophisticated threats targeting endpoints, and increasing regulatory compliance requirements around endpoint protections.
Size Of Endpoint Security Solution Market
There are various estimates on the size of the endpoint security solution market:
- Research firm Markets-and-Markets valued the total endpoint security market at $12.17 billion in 2020. They estimate this will grow to $18.37 billion by 2025, for a Compound Annual Growth Rate (CAGR) of 9.7%.
- Gartner reported that spending on endpoint protection platforms reached $3.37 billion in 2019. They forecast spending to reach $5.2 billion in 2024, reflecting strong growth.
- IDC estimates that the worldwide market for endpoint security software alone totalled $6.3 billion in 2020 and anticipates it reaching $8.9 billion in 2024.
To decide how best to tackle the issue of breaches originating at the endpoint, it is important first to understand the actual risks that they pose. Firstly, unprotected devices tend to be those that are used by remote workers, or as part of a BYOD agreement. This means that they have a lower security posture from the start, partly due to out-of-date anti-virus or internet security software or because they are shared with other users. In addition, they have a higher risk of compromise because they could be running counterfeit or unlicensed solutions, or they are operating from an untrusted network.
Hybrid or remote working exacerbates the risk. A survey carried out by SentryBay found that 42% of people working remotely had received suspicious emails and 18% had tackled a security breach. In addition, the survey found that 49% of remote employees felt vulnerable due to the insecurity of the endpoint devices they were using.
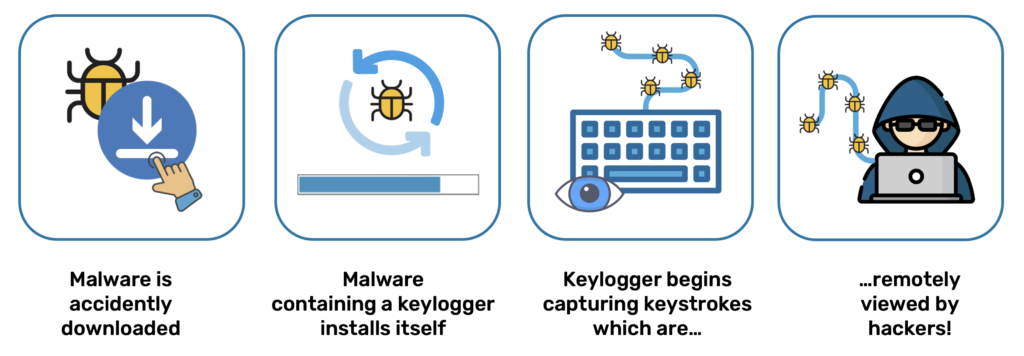
Unmanaged devices accessing a network remotely usually present a higher risk in terms of sensitive data including corporate login credentials. This sensitive data is at danger of being stolen via attacks involving keylogging. Along with spyware, keylogging is ranked as the highest risk malware by the NTT Security Threat Intelligence Report. Other types of attacks that endpoints are vulnerable to include screen capture / screen grabbing, man-in-the-browser, man-in-the-middle, DLL injection, and RDP double-hop. When it comes to endpoint security, protection against keylogging should be a priority. With a keylogger installed, it makes no difference how secure the data on an organisation server is, a breach can happen from the moment a user logs in and starts work.
How Keyloggers are Deployed via Malware
Protections Against Endpoint Keylogging
The most prevalent protections against endpoint keylogging currently are solutions such as AV (Anti-Virus) and EDR (Endpoint Detection and Response). Integral to both these technologies is malware detection. However, malware detection, particularly detection of newly released kernel-level malware, is now incredibly difficult and increasingly complex. The SANS Institute concluded that less than 50% of cyber-attacks are detected by antivirus software. Detection evasion techniques such as polymorphism and stealth-mode activation during sandboxing, results in fewer and fewer instances of new malware being detected.
Malware detection should not be relied upon exclusively. Rather, a layered approach to security should be taken (defence in depth), where multiple security controls compliment and reinforce each other. A layered approach provides strength and depth ensuring that although a specific attack may bypass one security measure, it will be thwarted by another. The most precious asset – data, and the specific applications which handle sensitive data – should be placed at the centre, with security layers wrapping it protectively.
New protection techniques which do not rely on detection, but securely wrap sensitive data and applications which process data, are now defined as “best of breed”. These do not wrap around the entire endpoint device, only the necessary applications – those that interact with sensitive data going into the cloud. Consider just how extensive the list of applications is, and what needs to be wrapped or secured in order to protect it: online office tools; SaaS application access; enterprise applications such as accounting, personnel, and CRM; SAP or Oracle applications and those remote access and remote desktop solutions such as Citrix, VMware, and Microsoft Azure. By securing the data that is entered into these applications, organisations are, in effect, ensuring that the unmanaged devices being deployed outside the corporate perimeter, are as secure (and in some case more secure) than standard managed corporate devices.
SentryBay’s Secure Framework
Utilising the Windows operating system to provision a new user or new desktop are low-overhead, easily provisioned methods of containerisation. The SentryBay secure framework employs a patent-pending process of limiting processes permitted to execute with the secure environment ensuring only trusted processes and applications are used. After use, the secure framework disappears leaving no trace.
The technology exists to ensure endpoints need not continue to be the weakest point in the organisation cloud ecosystem. Organisations can implement measures to minimise the likelihood of breach. By securing the input of sensitive data and by wrapping security around the applications which handle sensitive data, organisations can add another layer, boosting the protection of endpoint devices. In today’s world with more and more data being handled outside of the protection of the corporate perimeter, with BYOD, remote working and hybrid working, emerging technologies can help with both compliance and the overall security posture.





