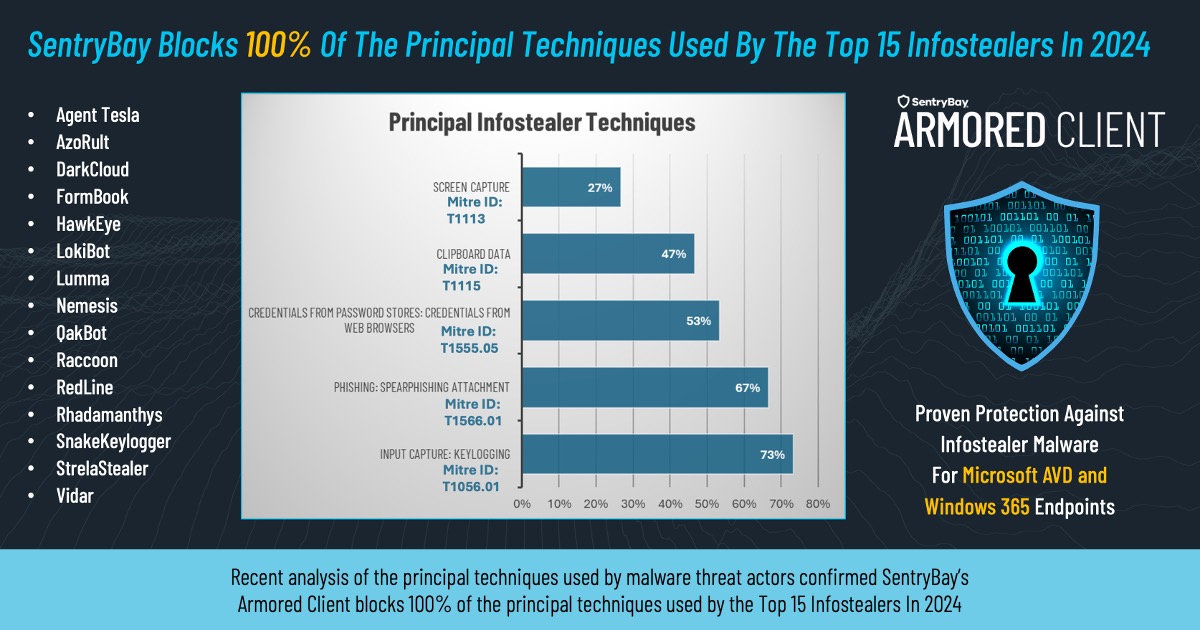
Recent analysis of the breach approaches used by malware threat actors confirmed SentryBay’s Armored Client blocks 100% of the principal techniques used by the Top 15 Infostealers In 2024.
SentryBay’s Cyber Defense Research Team identified keylogging as the number one method used to extract data from company / external assets (keylogging attack vector present in 73% of the 15 top infostealer strains of 2024).
Infostealer Attack Vectors
Additionally, SentryBay’s Armored Client delivers patented VDI/Browser isolation technology, which protects against all 6 attack vectors highlighted below:
- Screen Capture: T1113
- Process Injection: T1055
- Clipboard Data: T1115
- Credentials from Password Stores & Web Browsers: T1555.05
- Spear Phishing T1566.01
- Keylogging T1056.01
Additionally, cyber researchers have identified polymorphic keylogging malware as an emerging AI driven threat which is proven to evade industry leading EDR. SentryBay takes a preventative approach to these threats and leverages patented kernel-mode drivers to secure and isolate data in a unique way.
“This valuable research illustrates that AI-driven polymorphic keylogging attacks can evade traditional EDR. Enterprises need to re-evaluate their security posture with the future of AI-driven threats,” said Brent Agar, VP Strategic Partnerships, SentryBay. “SentryBay’s patented keylogging protection doesn’t require malware identification and encrypts every keystroke at the lowest level. This technology is the core of all its products.”
Proven Protection Against Infostealer Malware For Microsoft AVD And W365 Endpoints
SentryBay’s Armored Client is the OEM at the heart of Citrix App Protection, and is now proven protection against infostealer malware for Microsoft AVD and W365 endpoints. The solution utilises endpoint access isolation in a manner which does not impact on performance and includes Keylogging and Screen Capture protection.
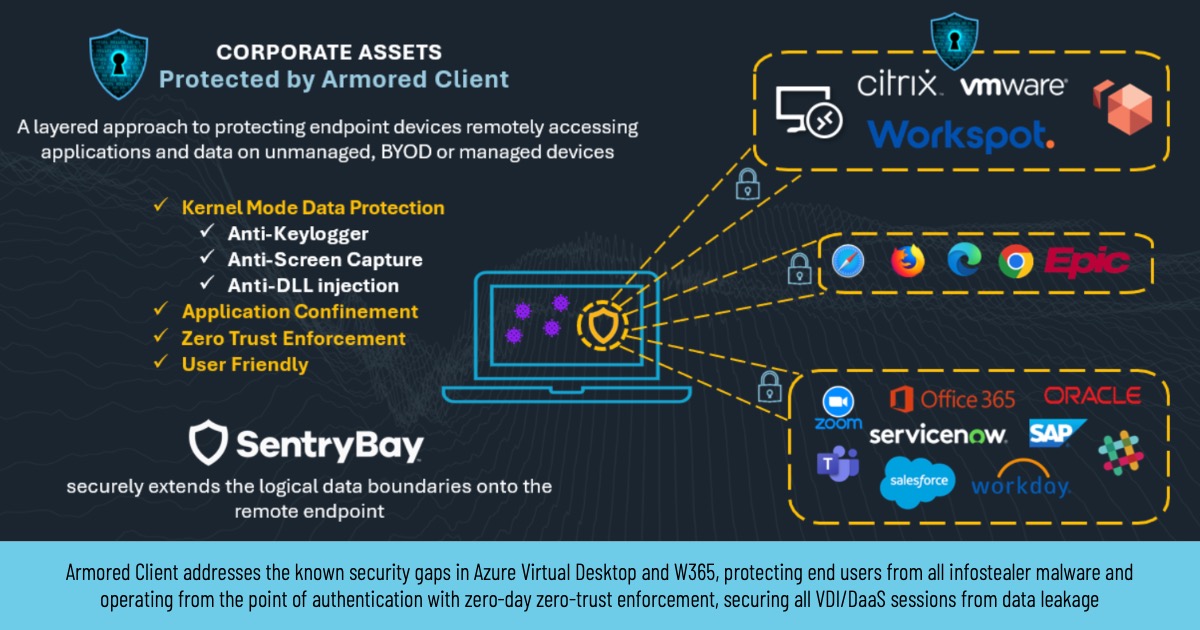
Armored Client addresses the known security gaps in Azure Virtual Desktop and W365, protecting end users from all infostealer malware and operating from the point of authentication with zero-day zero-trust enforcement, securing all VDI/DaaS sessions from data leakage, without infringing on end user privacy or disrupting user experience. Polymorphic AI can go undetected by EDR and XDR for months, so via its kernel mode protection and patented controls SentryBay’s Armored Client is the only solution able to protect AVD and W365 environments against Credential Theft, Keylogging, Screen Capture and Malicious Injection on the endpoint.



