
Malicious keyloggers are created to secretly capture keystrokes made by users. Imagine every keystroke you make on a keyboard – from login details to confidential information entered during a session – all this data can be collected and discreetly transmitted to a criminal group.
Keylogging attacks are on the rise. Recent notable cyberattacks involving the use of a keylogger include:
- In 2022, the hacker group Lapsus$ used a keylogger to steal source code from major tech companies like Microsoft, Okta, Nvidia and Samsung. The keylogger allowed them to covertly obtain credentials to access internal systems.
- A 2016 attack on cryptocurrency company Bitfinex saw cybercriminals use keyloggers to survey employees’ activities for months and drain about $60 million from user accounts.
- Hacker group DarkHotel infected hotel business centre computers from 2010-2020 with keyloggers, stealing data from high profile guests.
- In 2021, keylogger malware named CloudMensis was found pre-installed on Windows servers from Hewlett-Packard Enterprise. It enabled hackers to monitor keystrokes from remote admin sessions undetected.
- The Russia-linked APT29 hacking group used keylogger malware to steal email credentials from the US State Department and other government targets from 2019-2021.
- From 2018-2020, Iranian hackers conducted espionage using a custom keylogger named DanderSpritz against aerospace and petrochemical companies.
- The infamous 2017 NotPetya cyberattack that caused over $10 billion in global damages was initiated through a compromised accounting software update carrying a keylogger payload.
- In 2020 a phishing campaign involving emails claiming to be from the World Health Organisation installed the HawkEye keylogger on unsuspecting user’s computers.
- In 2020, the keylogger Olympic Vision was installed via phishing emails and Trojanized accounting software, to record keystrokes from accounting staff to steal corporate bank account credentials and facilitate wire transfer fraud. Over 18 organizations across banking, pharmaceuticals, in countries like Russia, the US, Germany and China were impacted.
- Keyloggers such as RedLeaves, InnfiRAT and QuasarRAT have been used over the past decade in targeted attacks against government, energy, and military entities.
One of the first software keyloggers ever developed was Keyboard Logger, an application written for Apple II systems by Perry Kivolowitz in 1983. By the late 1980s keylogger capabilities started appearing in early remote administration tools like Back Orifice and SubSeven. In the early 1990s commercial keylogger programs like Watcher and Keystroke Logger were advertised for sale online, marketed as employee monitoring tools. By the mid 1990s keylogger functions were built into some early malware like Casino, a Trojan that logged keystrokes to capture passwords. Today, most malware infestations include a keylogging component.
How Keyloggers Are Deployed Via Malware
Hackers may also deploy keyloggers through malware, often using phishing techniques like deceptive emails that trick users into clicking on malicious links to steal personal data including PINs, passwords, and other sensitive information.
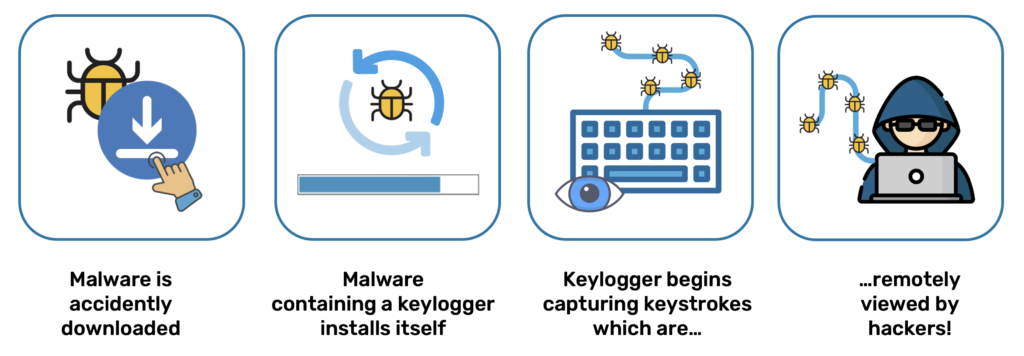
How Does A Keylogger Work?
Malicious keyloggers are designed to record keystrokes without the user being aware. Think of everything you enter on a keyboard – login credentials plus sensitive information entered during a session – all this data can be harvested and covertly sent to a criminal organisation.
Keyloggers have a role to play in advanced persistent threats (APTs), the sophisticated attacks that involve several intrusion methods, and are researched, customised, and focused for target organisations. The danger of APTs is that they extend over a prolonged period of months, quietly harvesting sensitive information with devastating effects on the victim organisation.
There are multiple forms of keylogger but the most difficult to detect work at the very core of the operating system – at the kernel. Advanced software development skills and a knowledge of writing kernel code are required to develop kernel-level keyloggers, and cyber gangs normally contract specialists for this task. Kernel-level keyloggers are deeply challenging to detect and eradicate, proving resistant to most standard security solutions such as conventional anti-virus software.
Protecting The Kernel With SentryBay
The most effective protection is a solution deployed by SentryBay which installs in the kernel as a keyboard filter driver which places itself first in the list of filters. The keyboard filter driver is then able to intercept keystrokes before they reach the keylogger, and replace actual keys entered by the user with fake, randomly generated characters. The keylogger then receives the random keystrokes rather than the real keystrokes. Solutions that enable this ensure that the driver filter order check is performed every time it runs and carry out an integrity check to ensure that the driver has not been tampered with.
Authentic keyboard entries are securely stored and encrypted in memory. Those entries are then only decrypted when the host application requests the inputted characters.
In this way, user keyboard entries are protected without identifying the malicious keylogger. If there is a malicious keylogger present on the system, it harvests only randomly generated keys which provide no information about the real keystrokes and the real data entered by the user.
Specialist Protection For A Specialist Threat
It is thought that over 90% of malware is polymorphic, having the ability to constantly adapt its makeup so that it evades detection, quarantine, and deletion. Kernel level keyloggers can change their signature frequently, and like other polymorphic malware, use encryption to hide their code.
Protecting data by replacing real keystrokes with fake random keystrokes should be performed whenever the user is interacting with sensitive data. In other words, this technique should be utilised when the user is browsing the internet or doing work through remote desktop software.
Keeping up with this level of challenge means thinking differently about protecting data entry and interjecting a barrier which allows keystrokes to be re-routed safely and encrypted. This is the only way that users can be sure that every time they enter a key on their keyboard, their personal data is not being collected at the kernel level and used for nefarious purposes.




