
Citrix is advising organizations to promptly install new updates following the discovery of two vulnerabilities in its NetScaler ADC and Gateway products. These vulnerabilities, known as CVE-2023-6548 and CVE-2023-6549, have emerged just a few months after the company faced challenges in containing the critical Citrix Bleed security flaw.
The CVE-2023-6549 vulnerability specifically involves a denial of service (DoS) issue in the NetScaler ADC and Gateway appliances. Rated with an 8.2 CVSS (Common Vulnerability Scoring System) score, this flaw is considered a high-severity vulnerability that can be exploited by hackers if the appliance is configured as a AAA virtual server or gateway.
Citrix Security Alert
Citrix recently published a security alert acknowledging the existence of a limited number of exploits for each vulnerability. Unfortunately, the company is currently unable to offer any mitigations or workarounds for this vulnerability. They are urging customers to promptly download and apply the permanent fixes that are available for NetScaler ADC and Gateway.
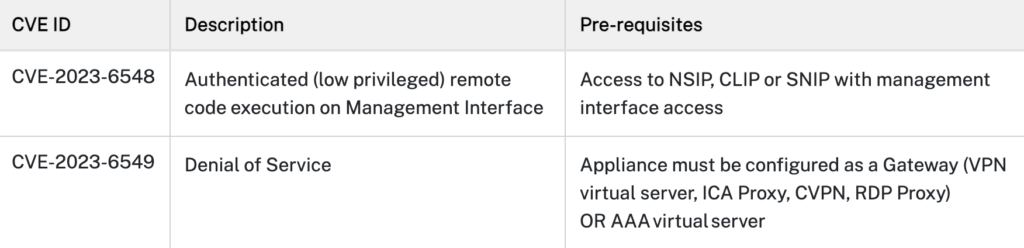
The vulnerability in question, CVE-2023-6548, is an authenticated remote code execution (RCE) exploit that targets the management interface. It has been classified as a 5.5 on the CVSS severity rating scale. According to The Register, “while all of this feels very Citrix-Bleed-esque, the vendor assures us that these new bugs under attack are not related to that zero-day.”
The severity rating may appear to be relatively low due to the condition that an authenticated attacker with limited privileges must have access to NetScaler IP (NSIP), Subnet IP (SNIP), or cluster management IP (CLIP) along with access to the system’s management interface to exploit this vulnerability. Cybersecurity researchers interviewed by ITpro urge customers to promptly install the suggested updates.
The Challenges Netscaler Faced in 2023 Continue to Persist
It is also advised to avoid exposing the management interface on the public internet and instead utilize a private network for hosting the NetScaler management IP. These precautions are crucial considering the recent discovery of CVE-2023-6548 and CVE-2023-6549, which mark the second and third vulnerabilities found in Citrix appliances within the last four months. As we move into 2024, it is evident that the challenges Netscaler faced in 2023 continue to persist.
“Of the two vulnerabilities, CVE-2023-6548, is likely to receive a significant amount of interest from threat actors,” said Tim Royston-Webb, CEO, SentryBay. “The vulnerability can be exploited by an authenticated attacker with low privileges if they are able to access NetScaler IP (NSIP), Subnet IP (SNIP), or cluster management IP (CLIP) with access to the appliance’s management interface.”
SentryBay Mitigates Against Netscaler Vulnerabilities
“Once a functional proof of concept is made public, the team at SentryBay anticipates a significant rise in the number of attempts to exploit this vulnerability,” commented Jeremy Greenwood, Enterprise Global Sales Lead, SentryBay. “The extent of the exploitation is currently uncertain, but it is expected to escalate substantially. Considering the anticipated interest in these vulnerabilities, it is likely that this will become evident within the next few months. In 2023 we have already seen several ransomware groups including LockBit, actively exploiting the previous critical Citrix Bleed security flaw in Citrix NetScaler ADC and Gateway appliances to obtain initial access to target environments within global businesses, including financial institutions and healthcare providers. However, Armored Client, SentryBay’s patented enforcement mechanism mitigates against Citrix Netscaler vulnerabilities. This ensures that sensitive data and business operations remain secure, even in the face of sophisticated cyber threats.”
SentryBay is ready to deliver protection to any organisations that need to shield sensitive data accessed via NetScaler.





