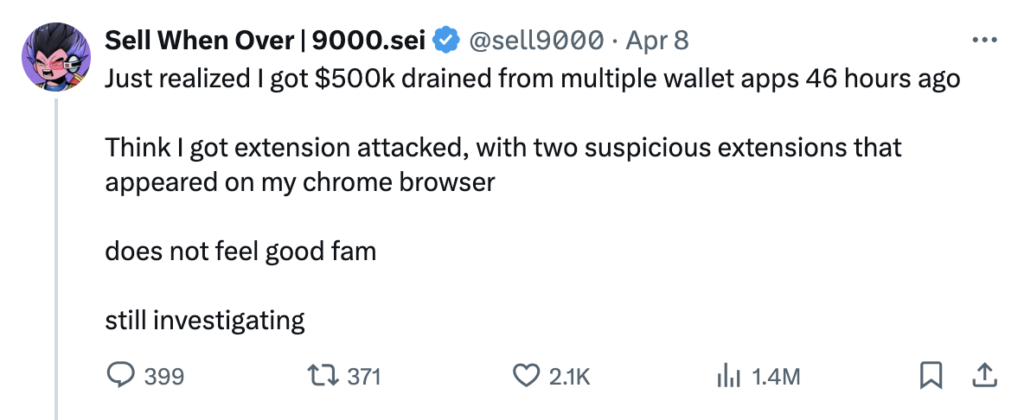
A cryptocurrency investor has claimed that “two suspicious extensions” potentially carrying a keylogger have siphoned off $800,000 from several of his wallet applications.
The individual, known as ‘sell9000’ on X (formerly Twitter), has resorted to the social media platform to ponder over the circumstances surrounding this occurrence.
Keylogger Targets Wallet Extension Apps
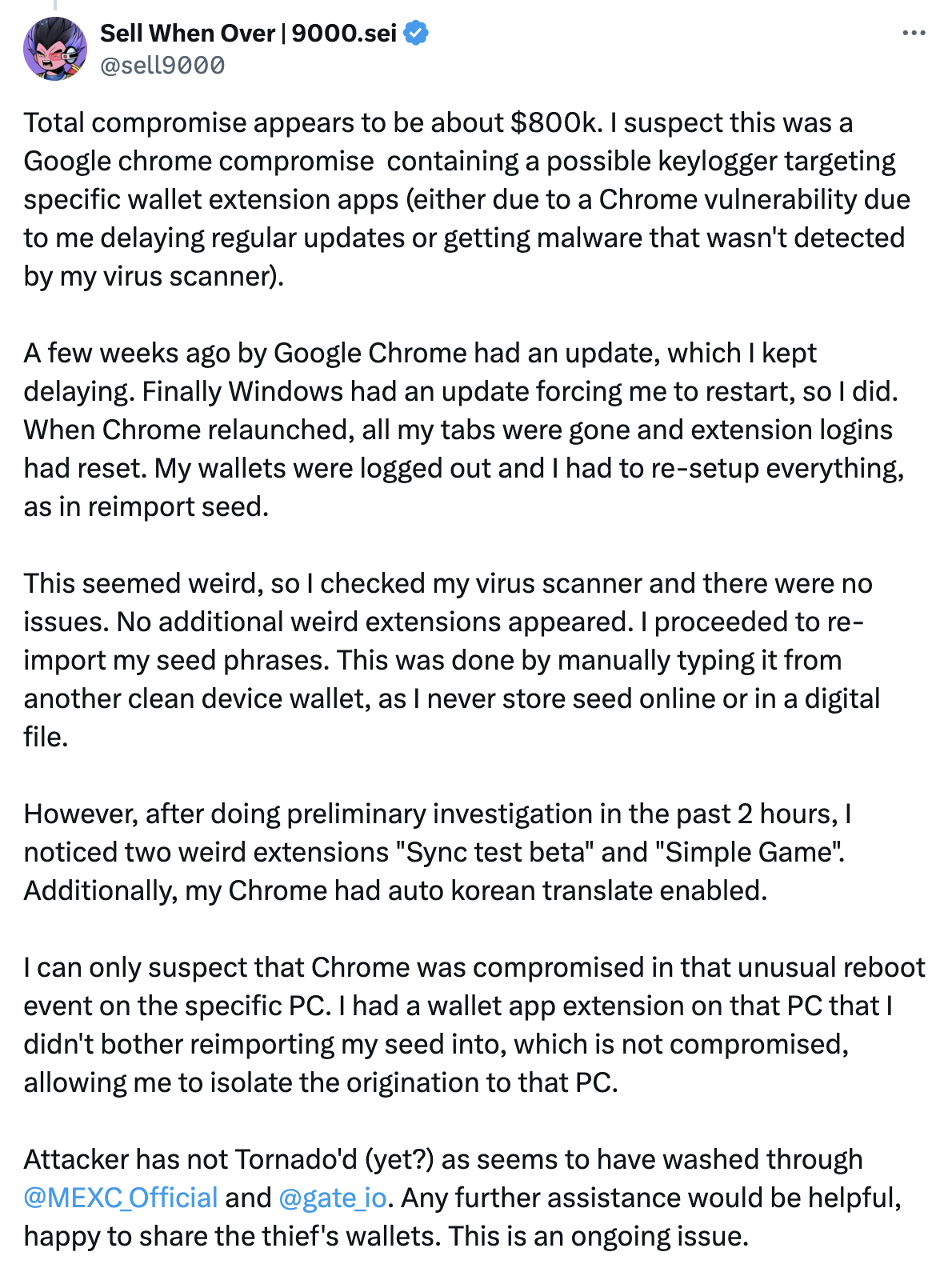
According to readwrite.com, it is his suspicion that there might have been a compromise in Google Chrome, which could potentially include a keylogger that specifically targets wallet extension apps. The individual detailed how he recently updated Google Chrome, only to find that “all my tabs were missing, and extension logins had been reset” upon reopening the browser. This also resulted in his wallets being logged out and needing to re-enter details.
A keylogger is a harmful software utilized by hackers to monitor and record every keystroke made by a user. The information collected can then be accessed by the individual running the logging program.
sell9000 asserts that Chrome was compromised during an uncommon reboot incident. The Crypto Times states, he discovered two extensions named ‘Sync Test Beta’ and ‘Simple Game.’ It has been reported that the hackers have transferred the funds to two exchanges, namely the Singapore-based MEXC exchange and the Cayman Islands-headquartered Gate.io. In a recent update, Sell9000 requests additional help and states that the issue is still ongoing.
Verified: Sync Test BETA Functions As Keylogger
The X user is currently uncertain about how the extensions were added to Chrome and the method of attack, but they have verified that ‘Sync Test Beta’ functions as a keylogger. On the other hand, ‘Simple Game’ is designed to monitor the status of tabs, including updates, openings, closures, and refreshes.
sell9000 considers the incident to be an “$800k costly mistake” and emphasizes that the key takeaway is to always err on the side of caution, especially when prompted to enter a seed – in such cases, it’s best to wipe the entire PC clean.
“My guard went down because the updated happened to be when Chrome made a significant update (where now you have to select a user and the[n] sign in with Google UI changed) so I thought that was what caused the extensions to reset and me to lose all my tabs,” commented sell9000 in Rmag.eu.
SentryBay Is Proven Defence Against Keylogger Threats
“The $800k loss suffered by sell9000 is a stark reminder that even the most security conscious individuals and organizations are not immune to keyloggers. They are insidious tools that can capture every keystroke, potentially leading to the compromise of sensitive information, including passwords and financial data,” said Brent Agar, VP Strategic Partnerships, SentryBay. “SentryBay’s patented Armored Browser solution delivers an additional security layer for online transactions and activities like cryptocurrency trading by creating a secure, isolated environment to protect against malicious browser extensions carrying keylogger payloads. The Armored Browser ensures that even if a user inadvertently installs a harmful extension, the integrity of sensitive information remains intact, blocking the extension’s ability to capture or manipulate data.”