IT administrators hold the responsibility of ensuring strong password policies and proper security measures are in place to prevent weak password practices. This includes establishing and maintaining robust password standards, implementing multi-factor authentication, and educating users on password security.
Neglecting these duties can lead to system vulnerabilities and breaches, making IT admins partially accountable. However, DarkReading reports that analysis of 1.8 million passwords highlighted 40,000 occurrences of the prevalence of ‘admin’ as the default password, which poses a significant security risk and are easy entry points for attackers.
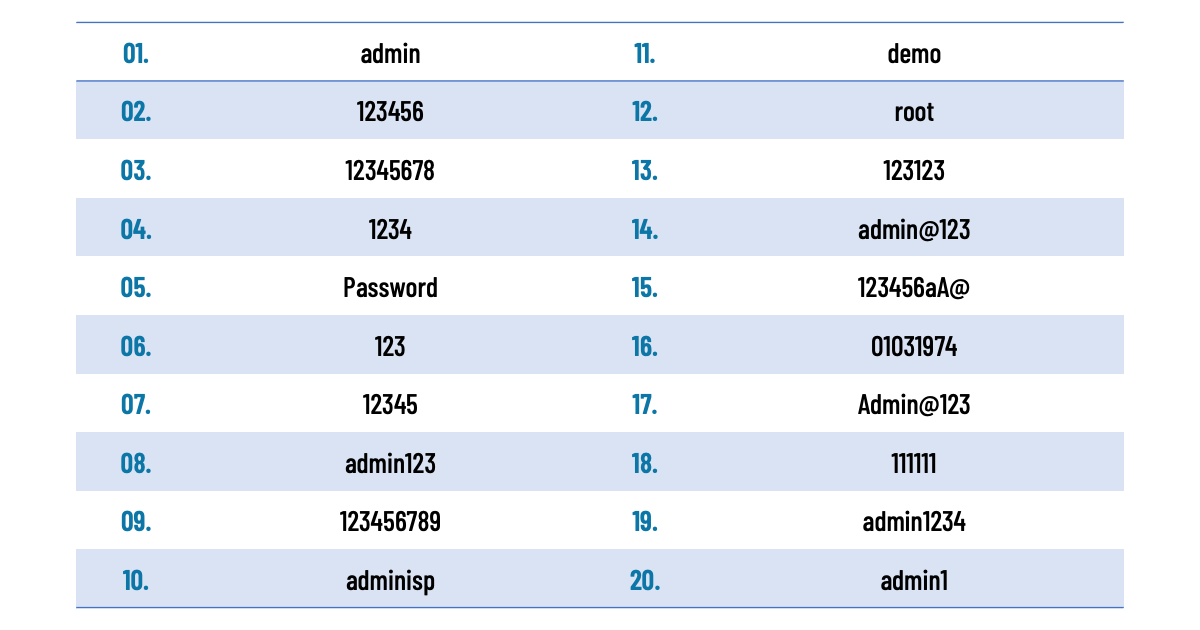
Despite recent legislation prohibiting the use of default passwords, unsophisticated attacks can still easily guess many of these passwords, emphasizing the importance of enforcing strong password policies. Reporting on the same research, BleepingComputer reveals the top 20 passwords consist of commonly used defaults and easily predictable options:
Businesses must act now
“This research revealing that over 40,000 admin portal accounts use ‘admin’ as a password is a call for businesses to act now. It’s imperative to use multiple fail safes to protect login credentials from sensitive data theft,” said Jeremy Greenwood, Enterprise Global Sales Lead, SentryBay. “SentryBay’s patented Endpoint Access Isolation technology takes the assumption that a device is already compromised and actively protects credentials and data no matter the strength or weakness of the password. SentryBay is a critical component of any enterprise’s security stack to supplement or supersede traditional credential protections.”




