The New Era of Visual Data Theft
While traditional malware once focused on files or keystrokes, today’s most advanced cyber threats have evolved far beyond. AI-powered screen capture malware is now among the most insidious and powerful data theft tools in use.
Instead of stealing files, these tools take repeated screenshots of what is actively displayed on a user’s screen. Then, using advanced Optical Character Recognition (OCR) engines and AI-based natural language processing, the malware interprets text, tables, numbers—even partial data—from these images. That text is converted into structured JSON objects, which are then quietly exfiltrated to an attacker’s server.
How It Works: Screenshot to JSON Extraction
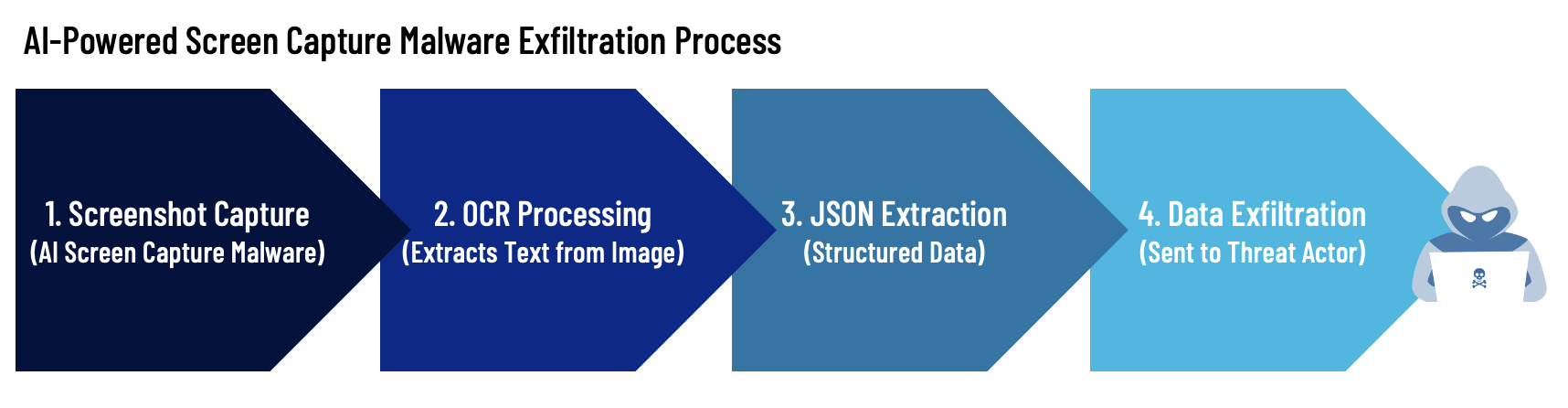
- Screen Capture Malware silently records screen contents at rapid intervals.
- AI OCR engines scan these images, extracting raw text, documents, credentials, and structured data from even brief visual exposure.
- JSON extraction enables the malware to structure this content into machine-readable databases.
- Exfiltration transmits these structured datasets to the attacker in real time, often without detection.
The Consequences at Scale
The ability to convert any screen content into machine-readable data means every type of information is at risk:
- Banking & Financial Services
Confidential financial data, transaction logs, customer credentials, and trading information can all be captured—resulting in identity theft, fraud, or insider trading risks. - Healthcare Institutions
Patient names, diagnoses, prescriptions, and insurance data are exposed in real-time—violating HIPAA and risking both regulatory penalties and patient trust. - Government Agencies
Sensitive communications, intelligence documents, or internal systems could be exposed—compromising national security or law enforcement operations. - Global Enterprises
IP addresses, customer records, R&D documentation, and proprietary data are extracted from screens—putting reputations and competitive advantage at risk.
All of this can occur even when files are encrypted and devices are considered “secure.” Why? Because AI malware no longer needs to decrypt files—it just needs to see them.
Why Traditional Defenses Fail
Most endpoint protection platforms focus on file access, process behavior, or system changes. Screen capture malware bypasses these by using legitimate system APIs to record what is already visible to the user. It’s stealthy, persistent, and often completely undetectable until it’s too late.
Worse, this malware doesn’t rely on static rules. With embedded AI, it adapts to content, learns patterns, and refines how it extracts valuable data over time.
The Proven Solution: SentryBay’s Armored Client
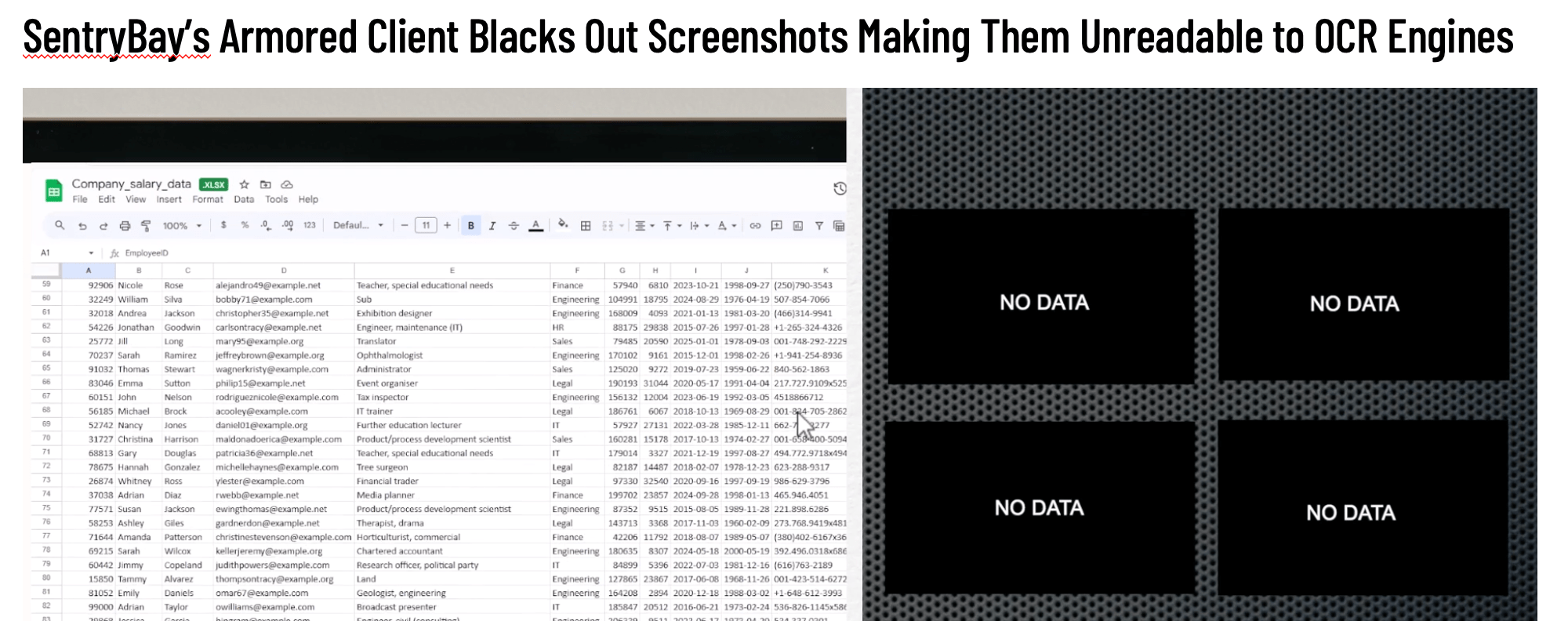
As the threat of AI-powered screen capture malware grows, global enterprises must adopt proactive defense models—tools that don’t wait for detection but actively prevent exfiltration.
SentryBay’s Armored Client is purpose-built for this new era of AI-driven cyber threats. It:
- Blacks out screen content at the system level, making screenshots unreadable to OCR engines.
- Neutralizes keylogging attempts by randomizing keystrokes before they touch the operating system.
- Prevents visual data theft across all applications, including VDI, browsers, and local apps—even when malware is already present.
“With the rise of AI-powered malware, protecting files is no longer enough,” commented Paul Gilbert, cybersecurity executive at SentryBay. “You must protect what is visible. Armored Client is the only endpoint solution that renders AI-driven screen capture attacks completely ineffective.”
SentryBay’s solution is now available to global enterprises, providing advanced security for any environment where sensitive data is displayed on screen. In a world where screenshots equal stolen data, blacking out the screen is the ultimate defense.




